OVH & the “Three Stooges” Approach to Network Abuse
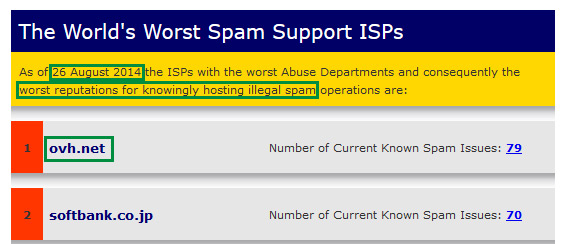
When you run a mail server and spend several hours a day blocking & reporting spam, patterns become noticeable after a while - in particular, which providers are good at addressing spam complaints. You also start to notice which providers are not so good at addressing spam complaints, which is how I first became aware of OVH Hosting. Before 2015, I was largely unaware of OVH - they are (or at least claim to be) the 3rd largest hosting provider in the world, but they are based in France and until recently they had operated primarily in that market, so I hadn't had much contact with them. They are well known in a few circles, however - in September of 2016, they were on the receiving end of a record-breaking distributed denial of service (DDoS) attack. They are also known for an even more dubious honour: in August of 2014, they were listed by SpamHaus as #1 on their list of "The World's Worst Spam Support ISPs".
As you may have already guessed, OVH ended up on my radar in May of 2015 when I started noticing a large volume of spam originating from their servers. These appeared to be different from a normal spam run, however, because the messages were almost all identical (spoofed/fake Kijiji alerts), and were being repeatedly sent to the same small number of EMail addresses. That approach is much more risky for the spammer, because it makes it much easier for their hosting provider to detect the spamming and shut down their account. In contrast, most spam are done in more of a fly-by-night fashion, where the spammers will try to send as many different spam EMails to as many different EMail addresses, in as short a time as possible - to get as much return on their "spamming investment" as possible before being shut down by their hosting provider. In fact, the behaviour of these spammers operating on the OVH network much more closely resembled that of spammers operating on "bulletproof" hosting providers, which refers to hosts that will not shut off customers, no matter how many abuse complaints they receive. Spammers using those types of providers typically take less precautions to hide their activities from their hosting provider, because they have reason to believe the hosting provider will turn a blind eye to the complaints.
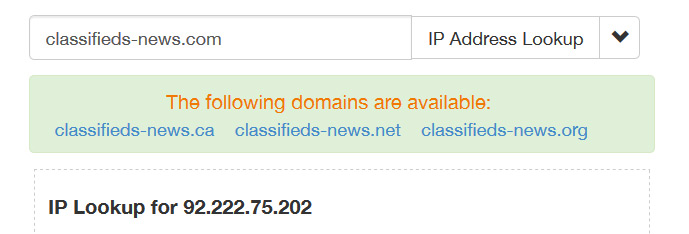
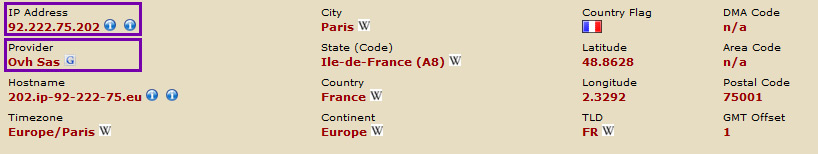
Because of those unusual details, I started looking into the content of the messages a little more closely. All of the Kijiji-spoofing spam contained links to spammy-looking domain names with uncommon TLDs like ".trade", ".loan", and ".bid", etc - and invariably, the links have all redirected to the website http://classifieds-news[dot]com (to avoid giving the spammers any kind of SEO-boost, we decided not to link to the site directly or publish it's domain without obfuscating it). The first surprise was that both the redirect links, and the site that they redirected to, were also hosted by OVH: the classifieds-news[dot]com domain name resolves to the IP address 92.222.75.202 - which according to lookup/geolocation services, is located in France and owned by the provider "Ovh Sas."
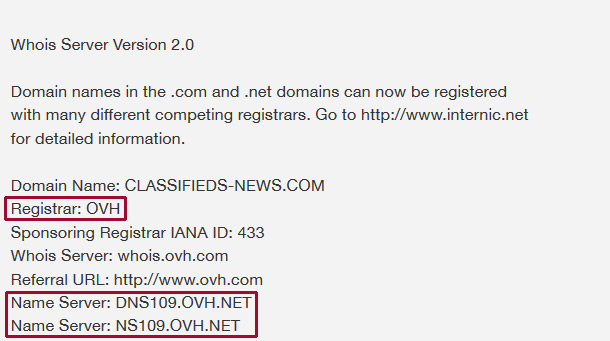
The owners of the site don't even bother to use CloudFlare or the like to hide where they're hosted, as the domain name is using the nameservers ns109.ovh.net and dns109.ovh.net - and OVH is also the registrar (registration provider) for the domain name, something it shares in common with the domains used for the redirect URLs.
So not only were the spammers using OVH's servers to send out junk EMail, but they were also using OVH to host the websites advertised in the spam and using OVH as the registrar for those sites' domain names. In other words, these spammers were effectively putting all of their eggs in one basket, and operating in way that would make it extremely easy for any competent, responsible hosting provider to detect and shut them down. And we're not the only the only ones to notice this particular spamming & spam support site: there's a post on the Fraud F.Y.I. blog from January 2017, noting that they've seen a large volume of the same spam with links that redirect to classifieds-news[dot]com - but impersonating Craiglist instead of Kijiji.
At first, we decided to treat the spam from OVH the same way we would treat spam from any other hosting provider: we reported the spam to them via Spamcop (a free reporting service that will analyze submitted spam EMails, identify which networks the spammers used, and allow you to easily send complaints to the people responsible for those networks). Several weeks went by without any response from OVH (which is, admittedly, typical for most large hosting providers) - and we continued receiving the spoofed Kijii alert spam, so we began reporting them directly to OVH by forwarding of all of the messages to abuse@ovh.net. Despite this, the spam continued - and still continues to this day. Does all of that mean that is OVH a "bulletproof" host? In fairness, no - in fact, there are numerous posts & forum threads around the web, where spammers & blackhat SEOs complain about OVH shutting down their accounts (though it is worth noting that that seems to be a recent change, since many of the complaints note that it didn't happen in the past). In this case, the saying "don't ascribe to malice what can be attributed to incompetence" would seem to apply - OVH appears to do the bare-minimum to deal with abuse complaints, and so far have only shut down the redirect URLs, while continuing to host the actual spam site that those URLs all redirect to: http://classifieds-news[dot]com, which is still active on OVH's server as of this writing. While they are likely also shutting down the accounts used to send the spam EMails, that does nothing to prevent those same spammers from setting up a new redirect URL, signing up for a new account, and continuing to send the same spam. In other words, OVH's abuse department appears to be only addressing the symptoms, while ignoring the cause & continuing to host the site that benefits from that spamming.
Even with OVH's "treat the symptoms, ignore the cause" approach, it has often taken them a week - or more - to take any action. In the fall of 2016, when the Kijii-spoofing spam restarted after a 2-3 month lull, we finally lost patience and decided to post about it on their forums; and as something of an experiment, we decided to keep track of how long the spam-vertised links remained active after they had been reported to OVH. We received another of the Kijiji-spoofing spam EMails from OVH's servers on January 14th of this year and posted the details on OVH's forums (as well as reporting it to them through Spamcop & their abuse-reporting address) - and it was not until January 19th (5 days later) that the spam redirect links were shut down. In contrast, shortly after the Kijiji-spoofing spam started up again, one of those EMails contained a link to a redirect URL hosted by a different provider - within 3 hours of reporting the link to them, we received a response from them stating that the offending site had been shut down (which we verified). A significantly faster turnaround than the roughly 120 hours that it took OVH to do the same thing, with a handful of forum replies being the only response we've received from them despite having reported dozens of near-identical spam from their servers over the course of nearly two years.
As we became more and more aware of the extent of the issue, and the extent of OVH's failure to address it, we start pressing them to either deal with the problem - or at the very least, provide an explanation. Unfortunately, the only responses we received were generic, stock excuses & attempts to downplay the issue. For example, one of the responses we received from "Phil" at OVH stated that "On first offences, we contact our customer and ask them to rectify the issue. If the the problem persists, only then will we take further action. This can sometimes take several days before the entire cycle completes itself" - which seemed incredibly disingenuous, given that the issue was FAR from being a first offense (closer to eightieth offense at that point), the fact that they had taken no effective action despite his claim to the contrary & despite the fact that the issue clearly had persisted, and the fact that the issue had continued well past the "several days" he claimed (unless you consider more than 500 days to be "several"). When we pointed out that literally none of the points in those 3 sentences had any relevance to the actual issue, Phil simply didn't respond. But even that was topped by OVH's response when we pointed out their history of having been listed as the World's Worst Spam Support ISP: Phil described that as "some problems [...] with spam," and attempted to paint it as just a temporary issue that they had "quickly rectified." He left our a "minor" detail, however: when OVH was listed as the #1 "World's Worst ISP," it was with 79 unresolved incidents - after reading Phil's claim that the issue had been rectified, I checked their current status on Spamhaus, which (as of December 12, 2016) listed: 72 unresolved issues - only 7 fewer than when they were on the top of the list. By every indication, they didn't drop off the Worst ISPs list because they actually rectified the issue, as claimed - but simply because they overtaken by even worse ISPs. Suffice it to say, we didn't receive any response after pointing that out either.
To sum up, and to highlight just how unusual this is: after nearly 20 years of being involved in the hosting industry, in various capacities, OVH is the only host I've ever encountered that allowed the same spammers to continue sending the same spam, to the same recipients, for nearly 2 years (not to mention hosting the site advertised by the spam). Which is all despite having been sent numerous abuse complaints, via 4 different methods: Spamcop reports, OVH's abuse reporting EMail, OVH's abuse reporting ticket system, and even publicly in their support forums. Yet the spamming has continued, averaging 1-2 per day; the only change is that these particular spammers appear to have stopped using OVH to host the redirect URLs and have started using WebSelf.net instead, a free website builder/hosting service based in Quebec (who don't seem to have a particularly fast turnaround for addressing spam complaints either). As one final last-ditch attempt, we started requesting return receipts & delivery status notifications when forwarding copies of the spam to OVH's abuse reporting address - and we did actually get a response, which was a pleasant surprise for a few seconds... until we looked at the details: the response was a notification that the message had been deleted without having been read. So far, we've received the same notifications from 2 different people at OVH (while it was tempting, we decided not to publish their names & EMail addresses). I honestly can't think of any better way they could have communicated a lack of concern for the issue, without stating it explicitly.
Before publishing this post, we of course attempted to provide OVH with the opportunity to comment: because OVH's contact page doesn't list any actual media contact info, we first attempted to reach them by posting on their forums, since that's the only place where we've received any response in the past - but after several days and two attempts, there has been no response. Following that, we made one final attempt to give them the opportunity to comment, by sending the same request to any official OVH EMail addresses we could find online (primarily in the WHOIS information for their domain names) - and if you've read this far, it probably won't be hard to guess what the result was: 24 hours & there's been no response. In the unlikely event that we do ever receive a response from them, we'll update this post.
It is also worth noting that this is only the most egregious example of spam/spam support that we've seen from OVH, and it's FAR from the being the only example: typically we receive at least 5-10 spam EMails every day that were either sent through OVH's mail servers, or advertise sites hosted by OVH (in many cases, it's both). And that's not even mentioning the other types of malicious traffic that we regularly receive from OVH's network: for example, the only brute-force attempts our servers have received from within Canada in the past year has been from OVH's network, with over 200 attempts in February 2017 alone - and there almost certainly would have been more if we didn't automatically ban IPs for repeated login failures. Amusingly, the volume of other malicious traffic may have actually reduced the spamming somewhat, since spammers wouldn't be able to send us EMail from servers/IP addressed that had already been blocked; to reference an old Simpsons episode, it's basically the "Three Stooges" approach to network abuse.
And while OVH's failures are the focus of this article, it should be noted that the owners of Classifieds-news[dot]com are almost certainly the people ultimately responsible for the spamming: either directly, or via third-party "EMail marketers" (which is almost always a euphemism for "freelance spammers"). The spam links take people to the site's homepage, with no affiliate/referral ID in the URL. True, it's possible that the spam is a "Joe job" (someone else sending spam advertising that site, in an attempt to get them kicked off their host or cause some other harm to them) - but it seems highly unlikely at this point, given how long it's gone on. If it is a "Joe job," then it's both incredibly persistent & incredibly ineffective (since it's evidently had no effect). Finally, it should be noted that OVH is not the only host providing spam support services for classifieds-news[dot]net (just the primary one), and none of them seem to take their responsibilities as internet hosts any more seriously than OVH does - including webself.net & their provider, Amazon AWS. But those are all topics for the follow-up article that we're working on.
Comments
StephenB on July 27 2017
@B. Berry - thanks!
If there’s some detail of the messages you receive that’s consistent from message to message (E.g. same subject, sender, originating mailserver, etc), then your hosting provider should be able to block those for you. I definitely wouldn’t expect OVH to do anything about it, based on our experiences with them.
Tim on November 15 2017
Hi, OVH cares more about taking the spammer’s money than people reporting the abuse. I’ve been bombarded with spam originating from OVH IP ranges, and also containing URLs hosted with OVH. I report daily via Spamcop, and continue to get the spam. I’ve resorted to blocking OVH IP classes, but is just of a pain process as having to take the time to report the spam daily (hourly!). They have an office in Montreal, if I lived closer, I’d be visiting them in person with a baseball bat!

B. Berry on July 27 2017
Interesting read. I have been having a problem with a site OVH Hosting hosts as well. “Whitecolorfine.life” which is sending out millions of spoofing e-mails daily. I personally receive 20 a day. Never had an e-mail problem with my e-mail account in 24 years till this showed up. As you, I have contacted and sent abuse reports with absolutely no response. This is not a reputable company at all. In reality OVH hosting is who should be shut down. I actually called these people on the phone and they refused to connect me with anyone at the company that could help me with this.