Google Drive Allows Malware to Remain Online for 91 Days (and counting) - [UPDATED 2017-11-10]

Recently, we've started seeing a new type of spam-driven EMail scam involving fake purchase orders. We've seen two or three different examples of the scam, but they all share some common traits: they come from GMail accounts (and one example use an Outlook.com address as the reply-to), the malicious files are hidden inside less-common archive formats such as .ACE and .REV (presumably to avoid detection by virus scanners), the spamming operation seems to be a bit more interactive in that they don't send the malware attachments/links unless you reply (presumably to avoid revealing their malware unless they think they have a "live one" on the hook), and they all use Google drive to host the files - in addition to sending them by EMail.
Naturally, we reported all of the offending GMail address & malicious Google drive links to Google (via Spamcop). Now, if you've read the title of this post - or you've ever personally tried to get Google to shut down malicious content/accounts in the past - then you can successfully guess what the result (or lack thereof) has been. But, if you're curious, read on for the details.
The first example of this spam that we received this summer arrived on August 8th: it came from someone claiming to be "jessie ganda" & using the EMail address purchasedepat1990@gmail.com - out of curiousity for how the scam worked, I decided to play along and reply. Two days later, on August 10th, the scammer replied by sending me a Google drive link to the supposed purchase order document - which was actually a .ACE archive containing a .EXE file (in other words, obvious malware).
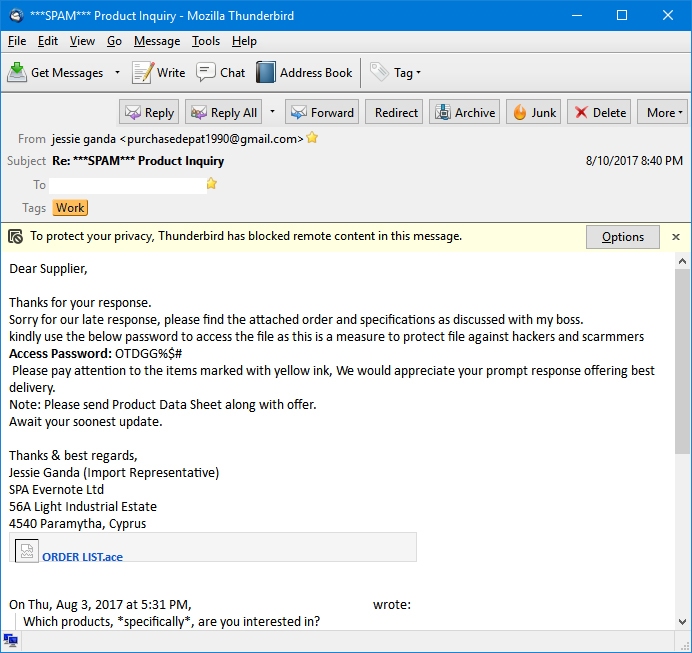
The link pointed to the URL https://drive.google.com/file/d/0BwKsklZY13s-a01QZUVpcUlvVDg/view - WARNING: that URL goes to page with a link to a malicious file that could seriously harm your computer if opened, the URL is included only for the purpose of documentation.
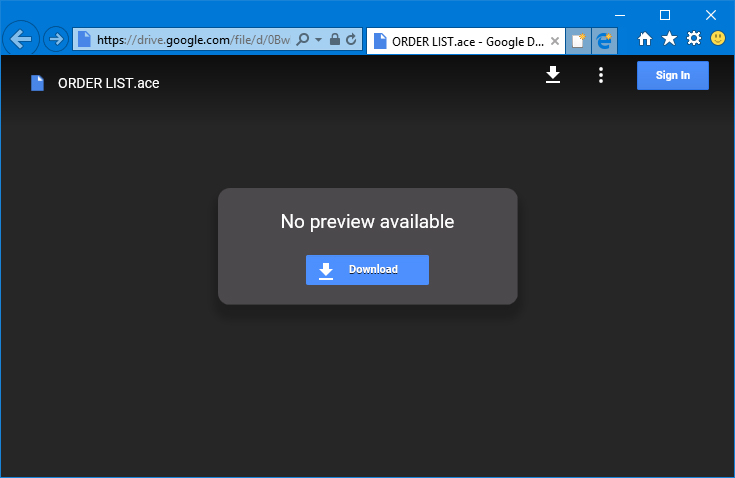
Both the link and the offending EMail address were reported to Google on the same day - August 10th. Yet as of the time of this writing, the link is still active and Google is still hosting the malicious file, and test messages sent to the purchasedepat1990@gmail.com don't bounce back, so it still appears to be active as well. For a multi-billion dollar, multinational tech company, taking that long to remove malware from their servers would be inexcusable even if they had actually dealt with the problem - which they haven't. Due to Google's continued failure to address any part of the issue, I've re-reported both spam EMails to them directly via the abuse@google.com & abuse@gmail.com addresses, as well as reporting the malicious file via the Google drive web interface.
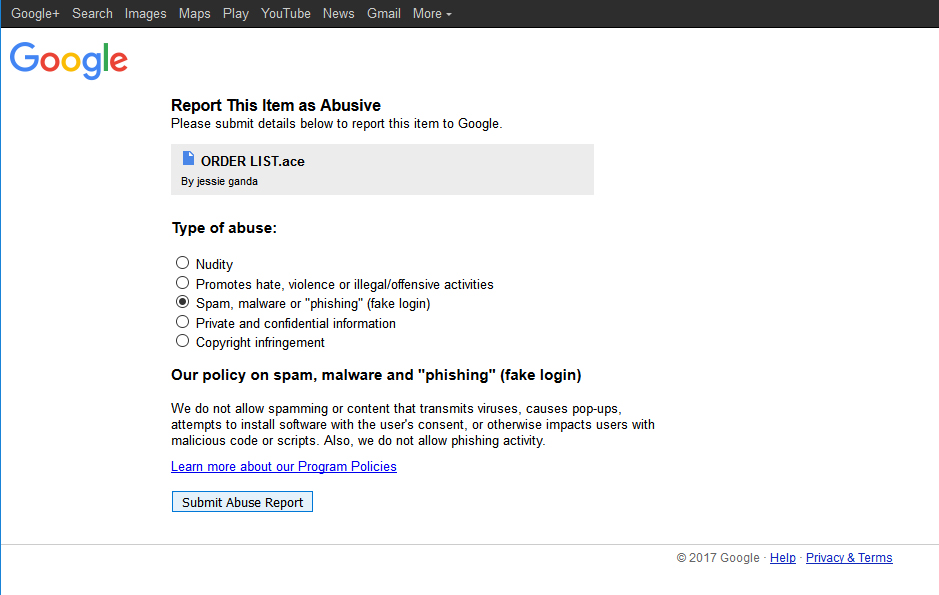
When (or if) Google gets around to actually doing anything about the malware they're knowingly hosting & the spam that they're facilitating, we'll update this article. Personally, I'm curious to see if they manage to address both parts of the issue (the spammer GMail account and the Google Drive-hosted malware), or if they pull an OVH and only deal with part of the problem.
UPDATE 2017-08-29: nearly a week has passed since this post was originally published - yet in that time, Google still has not done anything about the malicious files that they are hosting: the URL is still active (https://drive.google.com/file/d/0BwKsklZY13s-a01QZUVpcUlvVDg/view) and Google is still allowing downloads of the file. As such, given that the issue has been reported multiple times & was first reported more than two weeks ago, it appears that Google is knowingly allowing their servers to be used for distribution of malicious software.
It's also worth noting that the same group of spammers have sent us additional spam EMails (also from GMail accounts), containing a different to a malicious file, which of course is also hosted on Google Drive - and as should come as no surprise, Google hasn't done anything about that either (the offending GMail account still appears to be active, and the malicious file is still available for download). Given the circumstances, we've decided to give Google one more day to address the issue, which will be a full 20 days (four business weeks) since the issue was first reported - after that, we'll start re-resending reports of the spam EMails/accounts & the malicious files once per day and see how long it takes them to deal with the issues then.
UPDATE 2017-09-01: another three days have passed since the last update, and Google has still failed to take any evidence steps to address the issue (the malicious files are still available for download, and the GMail accounts that sent them still appear to be active) - bringing us to a total of 21 days since we first reported the issue to Google. Starting on August 30th, which was the 20 day point, we began reporting the malicious Google Docs link daily, using the "Report abuse" link on the same page - and so far, it appears that Google is ignoring those reports as well.
UPDATE 2017-09-06: another 5 days, and Google continues to allow the use of their servers to distribute malware - despite the previous reports that we sent, and the daily reports that we've been sending since August 30th. Right now, I'd put good odds on Google ignoring the issue for a full month - at that point, maybe we'll start sending them links to the malware via Twitter.
UPDATE 2017-09-25: nearly a month since the last update, aaaaaaaaaaand you guessed it - both of the Google Drive-hosted links to malicious files are still active (https://drive.google.com/file/d/0B4X7BhdRq1FMejE2aFpEbGViVmc/view and https://drive.google.com/file/d/0BwKsklZY13s-a01QZUVpcUlvVDg/view), AND all three of the GMail accounts used by the same spammers/scammers still appear to be active. So the lesson here seems to be: Google is perfectly happy to not only allow their EMail service to be used for spamming, but they also knowingly allow the use of Google Drive to distribute malware. And for the record, I'm giving Google the benefit of the doubt by assuming that they're aware of the issue - because the only other possibilities are even more damning: that Google (a multi-billion dollar multi-national company) is so badly-staffed/incompetently run that they literally aren't capable of responding to abuse complaints properly... or they simply don't care/can't be bothered, which is even less-excusable (also known as the "too big to fail" mentality).
UPDATE 2017-11-10: more than a month since the last update, and true to form, Google has still failed to do anything about the two Google drive-hosted malware links that we reported to them over 3 months ago (91 days... and counting). So, as a last-ditch attempt, we've sent Google a link to this article via Twitter. In the unlikely event that they ever get around to removing the malware that their servers are distributing, or at least responding to the post on Twitter, then we will update this post.


Jon DeGeorge on January 21 2019
2019-01-21:
The files are finally taken down!